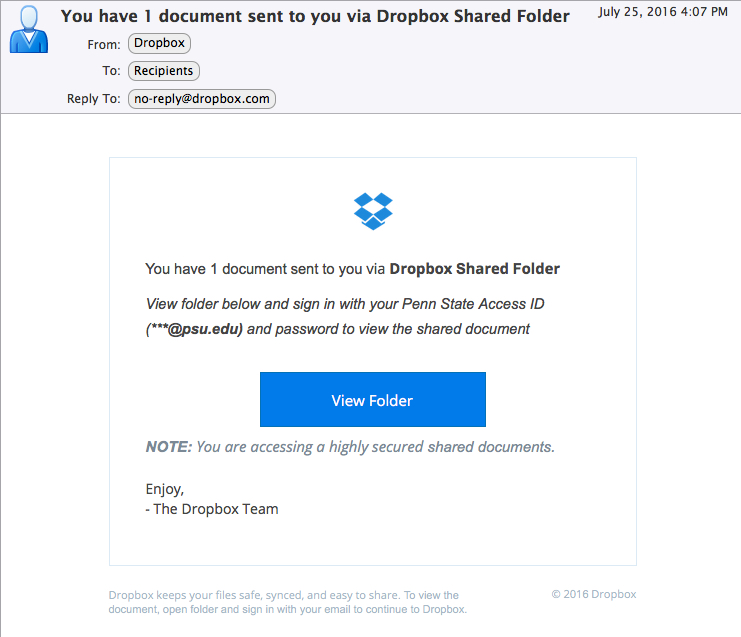
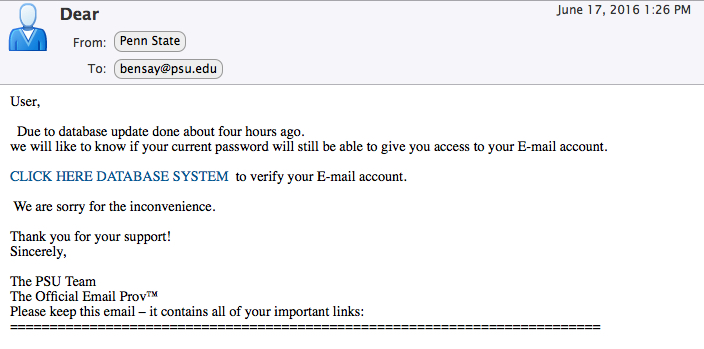
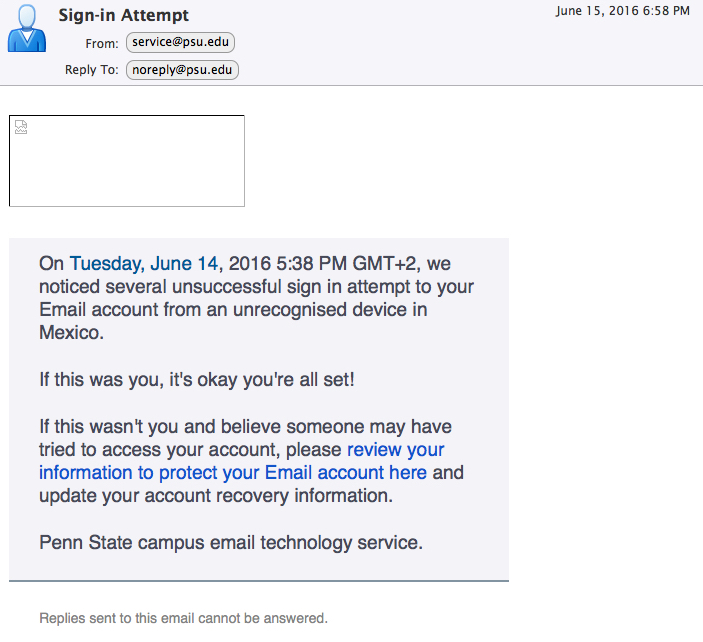
This phish provides several clues revealing it as a scam message:
- The “From” address is not actually a Penn State address
- The “To” address is the same as the “From” address, meaning that recipients were on a Bcc list
- The greeting is a generic “Dear User”
- The link appears to be a Penn State link when you look at it, but it actually goes to an address in the joshuafitzgerald.com domain, which has nothing to do with Penn State
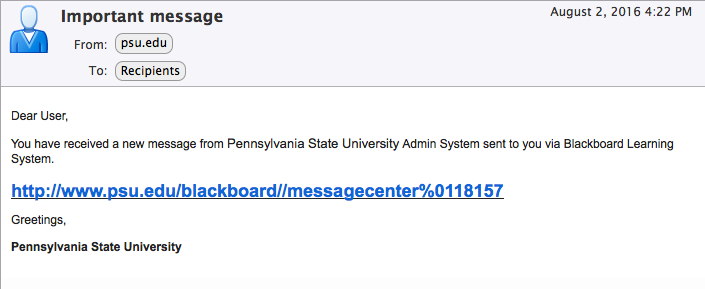
From: “psu.edu” <xxxxxx@ccri.edu>
Date: Tuesday, August 2, 2016 at 4:22 PM
To: Recipients <xxxxxx@ccri.edu>
Subject: Important message
Dear User,
You have received a new message from Pennsylvania State University Admin System sent to you via Blackboard Learning System.
http://www.psu.edu/blackboard//messagecenter%0118157 <– Links to a fake Blackboard login page in the joshuafitzgerald.com domain
Greetings,
Pennsylvania State University